We all know that the SY0-601 exam dumps make it easy to earn CompTIA Security+ certification. But forget the most important point: SY0-601 exam dumps are up-to-date, and any expired dumps are garbage.
Pass4itSure has released new SY0-601 exam dumps https://www.pass4itsure.com/sy0-601.html to ensure a smooth process to help you prepare for the exam, and the latest SY0-601 exam dumps are excellent SY0-601 study material.
Do you know about the CompTIA Security+ exam 2022?

Information about the CompTIA Security+ 2022 exam:
The SY0-601 exam measures knowledge and skills to prevent, detect, and mitigate system and cyberattacks. You need to answer 90 questions in the allotted 90 minutes and score 750 points to pass the exam successfully.
SY0-601 exam questions are mostly multiple-choice and performance-based. The exam costs $392.
How to study for the SY0-601 exam effectively?
Tips for effective exam study: Use the latest SY0-601 study materials, such as Pass4itSure newly released SY0-601 exam dumps.
With it, it serves as study material for the SY0-601 exam. Practice SY0-601 exam questions diligently to ensure a successful pass of the CompTIA Security+ 2022 exam.
Why do the SY0-601 pdf dumps provide effective exam preparation?
Because the SY0-601 pdf dumps have fully verified CompTIA SY0-601 exam questions, it helps us understand the exam content well and pass it more easily.
You can get the free SY0-601 dumps pdf (latest version) here: https://drive.google.com/file/d/1K34tTP8WCdNOxo2OUrlqscdaEirpTVDZ/view?usp=share_link
Where can I find free CompTIA Security+ SY0-601 exam questions to practice?
Here, you will find the latest SY0-601 exam questions.
Free SY0-601 dumps perfect exam questions 1-13
Latest questions 1
A system administrator needs to implement an access control scheme that will allow an object\\’s access policy be determined by its owner. Which of the following access control schemes BEST fits the requirements?
A. Role-based access control
B. Discretionary access control
C. Mandatory access control
D. Attribute-based access control
Correct Answer: B
Latest questions 2
DRAG DROP
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
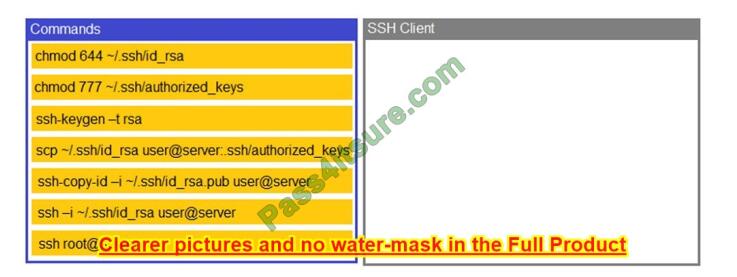
Correct Answer:
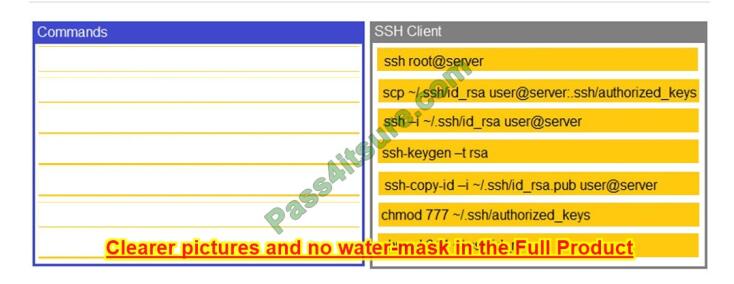
Latest questions 3
Organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an anomalybased system. Which of the following does the organization need to determine for this to be successful?
A. The baseline
B. The endpoint configurations
C. The adversary behavior profiles
D. The IPS signatures
Correct Answer: A
Latest questions 4
After consulting with the Chief Risk Officer (CRO). a manager decides to acquire cybersecurity insurance for the company Which of the following risk management strategies is the manager adopting?
A. Risk acceptance
B. Risk avoidance
C. Risk transference
D. Risk mitigation
Correct Answer: C
Latest questions 5
Which of the following environments utilizes dummy data and is MOST likely to be installed locally on a system that allows code to be assessed directly and modified easily with each build?
A. Production
B. Test
C. Staging
D. Development
Correct Answer: B
Latest questions 6
A host was infected with malware. During the incident response, Joe, a user, reported that he did not receive any emails with links, but he had been browsing the Internet all day. Which of the following would MOST likely show where the malware originated?
A. The DNS logs
B. The web server logs
C. The SIP traffic logs
D. The SNMP logs
Correct Answer: A
Latest questions 7
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic.
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
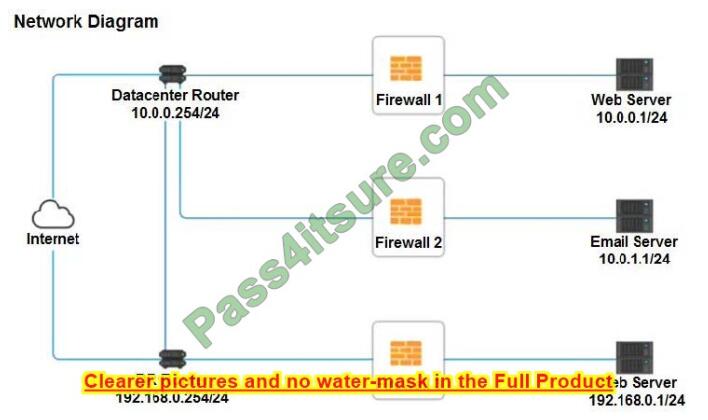
Firewall 2
Hot Area:
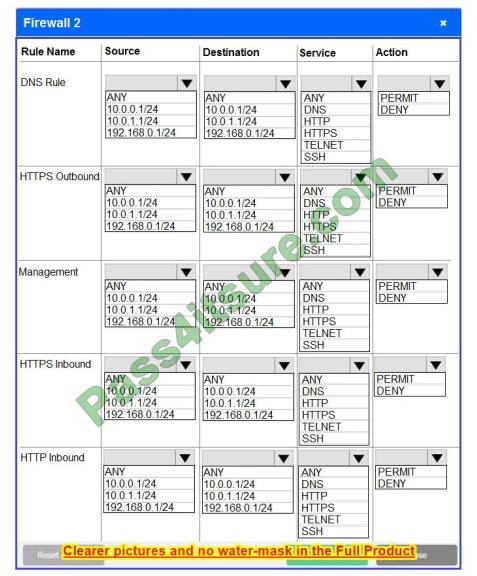
Correct Answer:
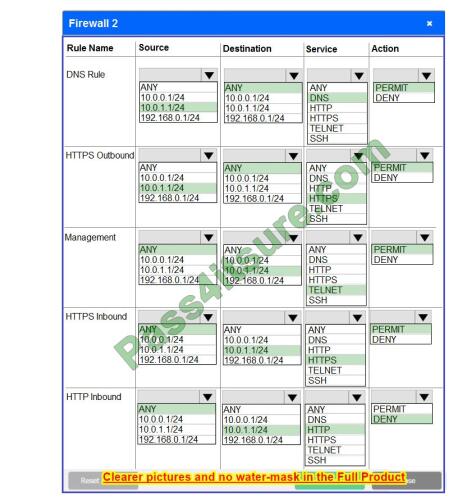
Firewall 2: No changes should be made to this firewall

Latest questions 8
An organization is having difficulty correlating events from its individual AV. EDR. DLP. SWG. WAF. MOM. HIPS, and CASB systems. Which of the following is the BEST way to improve the situation?
A. Remove expensive systems that generate few alerts.
B. Modify the systems to alert only on critical issues.
C. Utilize a SIEM to centralize togs and dashboards.
D. Implement a new syslog/NetFlow appliance.
Correct Answer: C
Latest questions 9
Which of the following technical controls is BEST suited for the detection and prevention of buffer overflows on hosts?
A. DLP
B. HIDS
C. EDR
D. NIPS
Correct Answer: C
Latest questions 10
The Chief Information Security Officer warns lo prevent exfiltration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the BEST solution to Implement?
A. DLP
B. USB data blocker
C. USB OTG
D. Disabling USB ports
Correct Answer: C
Latest questions 11
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:
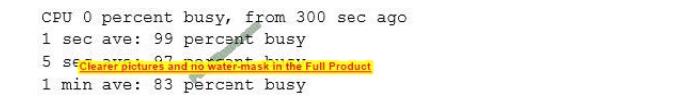
Which of the following is the router experiencing?
A. DDoS attack
B. Memory leak
C. Buffer overflow
D. Resource exhaustion
Correct Answer: D
Latest questions 12
Which of the following would produce the closet experience of responding to an actual incident response scenario?
A. Lessons learned
B. Simulation
C. Walk-through
D. Tabletop
Correct Answer: B
Latest questions 13
An attacker was easily able to log in to a company\’s security camera by performing a basic online search for a setup guide for that particular camera brand and model Which of the following BEST describes the configurations the attacker exploited?
A. Weak encryption
B. Unsecure protocols
C. Default settings
D. Open permissions
Correct Answer: C
Always choose the latest study materials to prepare for the SY0-601 exam. Pass4itSure has updated the SY0-601 exam dumps, come and use the latest SY0-601 exam dumps https://www.pass4itsure.com/sy0-601.html easily earn CompTIA Security+ certification.