For those who take the exam, please see here. We have prepared the latest CAS-004 exam dumps for the CompTIA CAS-004 exam.
We are confident that the latest CAS-004 exam dumps questions and answers we provide you with are valid CASP+ CAS-004 exam material to guide you to success in the CASP+ CAS-004 exam.
Use the Pass4itSure CAS-004 exam dumps address: https://www.pass4itsure.com/cas-004.html (Updates 2022.9) to obtain a successful CompTIA Advanced Security Practitioner (CASP+) exam.
first of all, to figure out CompTIA CASP+, pass the CAS-004 exam?
Yes, this is closely related to CAS-004, and you have to figure it out.
The CompTIA Advanced Security Practitioner (CASP+) consists of two exams:
- CAS-003
- CAS-004
Note that the CAS-003 exam will retire by the following dates
April 5, 2022 (English version)
December 31, 2022 (Japanese)
CAS-003 vs CAS-004, the specific comparison between the two is shown in the following figure
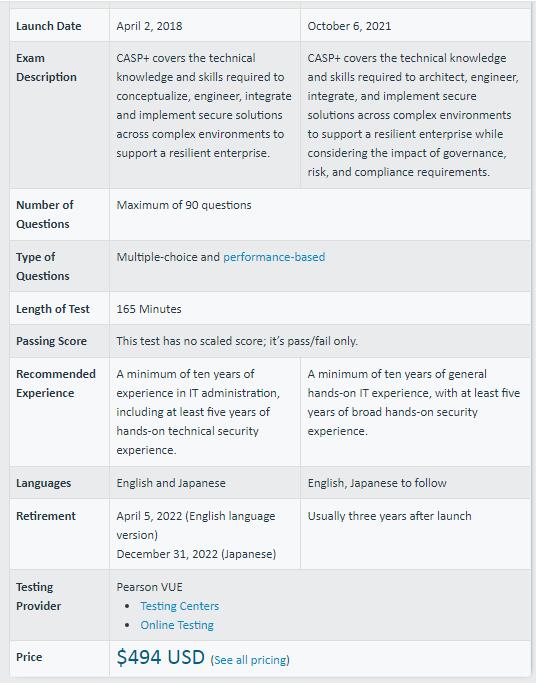
How to summarize the CASP+ CAS-004 exam in one sentence?
The CAS-004 exam is a 165-minute test with 90 or so questions that you need to answer. There is no specific score for passing, only passing/failing. The exam is available in English and Japanese and costs $494. Successfully passing the CAS-004 exam results in CompTIA Advanced Security Practitioner certification.
How can I effectively prepare for the CAS-004 exam and improve my learning ability?
The availability of valid CASP+ CAS-004 exam material determines the success of the exam.
You may ask, how to choose a valid CAS-004 exam material, don’t worry, here will tell you, you can rest assured that you can use the Pass4itSure CAS-004 exam dumps provided by the effective (CASP+) CAS-004 exam material, it will really effectively lead you to study and successfully pass.
Looking for free CAS-004 exam materials?
Here you will find online CAS-004 exam tests and CAS-004 PDF files available for you.
For more free questions about other exams in the CompTIA series, please visit downloadzpdf.com.
Real and valid CompTIA CAS-004 dumps PDF material is free to download: https://drive.google.com/file/d/12FygZbfE0wiD7VKkvdJT8drDjDOokjBE/view?usp=sharingFor more free questions about other exams in the CompTIA series, please visit downloadzpdf.com
Free CompTIA CAS-004 Exam Dumps Questions
Q1/ A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of assets, such as workstations, servers, and laptops. Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the company?
A. Increased network latency
B. Unavailable key escrow
C. Inability to select AES-256 encryption
D. Removal of user authentication requirements
Correct Answer: A
Q2/ A junior developer is informed about the impact of new malware on an Advanced RISC Machine (ARM) CPU, and the code must be fixed accordingly. Based on the debug, the malware is able to insert itself into another process memory location. Which of the following technologies can the developer enable on the ARM architecture to prevent this type of malware?
A. Execute never
B. No-execute
C. Total memory encryption
D. Virtual memory encryption
Correct Answer: A
Reference: https://developer.arm.com/documentation/102433/0100/Stack-smashing-and-execution-permissions
Q3/ A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time. Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
A. The company will have access to the latest version to continue development.
B. The company will be able to force the third-party developer to continue support.
C. The company will be able to manage the third-party developer\’s development process.
D. The company will be paid by the third-party developer to hire a new development team.
Correct Answer: B
Q4/ A health company has reached the physical and computing capabilities in its data center, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare applications that process sensitive health and payment information. Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standards for virtualization and cloud computing?
A. Hybrid IaaS solution in a single-tenancy cloud
B. Pass solution in a multitenancy cloud
C. SaaS solution in a community cloud
D. Private SaaS solution in a single tenancy cloud.
Correct Answer: D
Q5/ Device event logs sources from MDM software as follows:
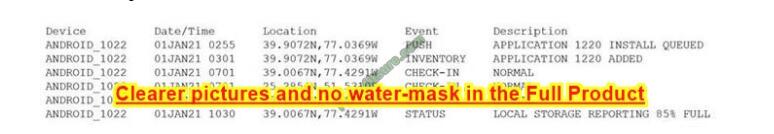
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
A. Malicious installation of an application; change the MDM configuration to remove application ID 1220.
B. Resource leak; recover the device for analysis and clean up the local storage.
C. Impossible travel; disable the device\\’s account and access while investigating.
D. Falsified status reporting; remotely wipe the device.
Correct Answer: A
Q/6 A recent data breach stemmed from unauthorized access to an employee\’s company account with a cloud-based productivity suite. The attacker exploited excessive permissions granted to a third-party OAuth application to collect sensitive information. Which of the following BEST mitigates inappropriate access and permissions issues?
A. SIEM
B. CASB
C. WAF
D. SOAR
Correct Answer: C
Reference: https://www.cloudflare.com/en-gb/learning/ddos/glossary/web-application-firewall-waf/
Q/ 7 A Chief Information Officer (CIO) wants to implement a cloud solution that will satisfy the following requirements:
1. Support all phases of the SDLC.
2. Use tailored website portal software.
3. Allow the company to build and use its own gateway software.
4. Utilize its own data management platform.
5. Continue using agent-based security tools.
Which of the following cloud-computing models should the CIO implement?
A. SaaS
B. PaaS
C. MaaS
D. IaaS
Correct Answer: D
Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
Q/ 8 The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls. The following configurations already are in place:
1. Keyword blocking based on word lists
2. URL rewriting and protection
3. Stopping executable files from messages
Which of the following is the BEST configuration change for the administrator to make?
A. Configure more robust word lists for blocking suspicious emails
B. Configure appropriate regular expression rules per suspicious email received
C. Configure Bayesian filtering to block suspicious inbound email
D. Configure the mail gateway to strip any attachments.
Correct Answer: B
Reference: https://www ibm.com/docs/en/rsoa-and-rD/36?tODic=Darsing-extension-customization
Q/ 9 A home automation company just purchased and installed tools for its SOC to enable incident identification and response on software the company develops. The company would like to prioritize defenses against the following attack scenarios:
Unauthorized insertions into application development environments Authorized insiders making unauthorized changes to environment configurations. Which of the following actions will enable the data feeds needed to detect these types of attacks on development environments? (Choose two.)
A. Perform static code analysis of committed code and generate summary reports.
B. Implement an XML gateway and monitor for policy violations.
C. Monitor dependency management tools and report on susceptible third-party libraries.
D. Install an IDS on the development subnet and passively monitor vulnerable services.
E. Model user behavior and monitor for deviations from normal.
F. Continuously monitor code commits to repositories and generates summary logs.
Correct Answer: CD
Q/ 10 A company is preparing to deploy a global service. Which of the following must the company do to ensure GDPR compliance? (Choose two.)
A. Inform users regarding what data is stored.
B. Provide opt-in/out for marketing messages.
C. Provide data deletion capabilities.
D. Provide optional data encryption.
E. Grant data access to third parties.
F. Provide alternative authentication techniques.
Correct Answer: AB
Reference: https://gdpr.eu/compliance-checklist-us-companies/
Q/ 11 Which of the following is the MOST important security objective when applying cryptography to control messages that tell an ICS how much electrical power to output?
A. Importing the availability of messages
B. Ensuring non-repudiation of messages
C. Enforcing protocol conformance for messages
D. Assuring the integrity of messages
Correct Answer: D
Q/ 12 A forensic expert working on a fraud investigation for a US-based company collected a few disk images as evidence. Which of the following offers an authoritative decision about whether the evidence was obtained legally?
A. Lawyers
B. Court
C. Upper management team
D. Police
Correct Answer: A
Q/ 13 A financial institution has several that currently employ the following controls:
1. The severs follow a monthly patching cycle.
2. All changes must go through a change management process.
3. Developers and systems administrators must log into a jump box to access the servers hosting the data using two-factor authentication.
4. The servers are on an isolated VLAN and cannot be directly accessed from the internal production network. An outage recently occurred and lasted several days due to an upgrade that circumvented the approval process. Once the security team discovered an unauthorized patch was installed, they were able to resume operations within an hour.
Which of the following should the security administrator recommend to reduce the time to a resolution if a similar incident occurs in the future?
A. Require more than one approver for all change management requests.
B. Implement file integrity monitoring with automated alerts on the servers.
C. Disable automatic patch update capabilities on the servers
D. Enhanced audit logging on the jump servers and ship the logs to the SIEM.
Correct Answer: B
Get more CompTIA Advanced Security Practitioner (CASP+) CAS-004 exam dumps questions on this website.